How To Prevent Malware—Essential Security Tips for Every Internet User
Malware is a growing cybersecurity concern that affects individuals and businesses alike— according to the Annual Website Security Report by SiteLock, almost 4.1 million websites are infected with malware at any given moment[1].
With cybercriminals continuously developing new tactics to breach people’s and companies’ security, staying safe requires proactive measures. In this guide, we’ll provide practical tips on how to prevent malware from infiltrating your devices. You’ll learn to recognize risky behavior, block infections before they happen, and protect your data beyond traditional security tools.
How Does Malware Work?

Malware is a general term for any harmful software present on your device without your knowledge or consent. It typically spreads through harmful links or attachments, fake software downloads, compromised websites, or corrupted drives (like USB sticks).
If a cybercriminal manages to deliver malware on your device, they can use it to:
- Steal your account or financial data (saved passwords, card details, banking logins)
- Hijack devices (for spam, crypto mining, or ransomware attacks)
- Spy on activity (keyloggers, screen recorders)
Once executed, malware can often self-replicate throughout the system, blocking access to files or the entire system, displaying unwanted advertisements, or breaking essential system components.
Malware isn't limited to computers—mobile phones, tablets, security cameras, and other IoT devices are equally vulnerable to infection through malicious apps and websites or network exploits.
What Are the Most Common Types of Malware?
Cybercriminals deploy various forms of malicious software, each designed with particular objectives and infection methods. Here are the most common types of malware:
Signs Your Device May Be Infected With Malware
While symptoms can vary depending on the type of malware, these common indicators may suggest your device is compromised:
- Unusually slow performance or random system crashes
- Unexpected pop-ups or ads, especially outside your browser
- Sudden battery drain (common on phones and laptops due to background malware activity)
- Suspicious applications or browser toolbars that appear without installing them
- High network activity even when you're not actively using the internet
- Disabled security software or inability to update your OS
Some sophisticated malware (like spyware) can operate completely undetected, which may be even more dangerous. These stealthy threats can silently steal sensitive data for months before you notice, giving cybercriminals ample time to exploit your personal information while leaving no obvious traces of compromise.
How To Protect Your Computer From Malware Attacks
Protecting your devices from malware requires layers of protection that work together to block, detect, and neutralize threats. Here are five ways to prevent malware that can help safeguard your devices and data:
- Keep all software and operating systems updated
- Use reputable anti-malware software
- Practice safe browsing and download habits
- Secure your network
- Regularly back up important files
Keep All Software and Operating Systems Updated
Cybercriminals often exploit security flaws and vulnerabilities in apps and systems to gain unauthorized access to your device. These weak spots can exist in anything from your operating system to your browser or PDF reader.
To eliminate these known entry points, you should enable automatic updates for your operating system (Windows, macOS, iOS, or Android) whenever possible. For other applications, such as browsers, PDF readers, and productivity tools, checking for updates weekly is recommended.
Use Reputable Anti-Malware Software
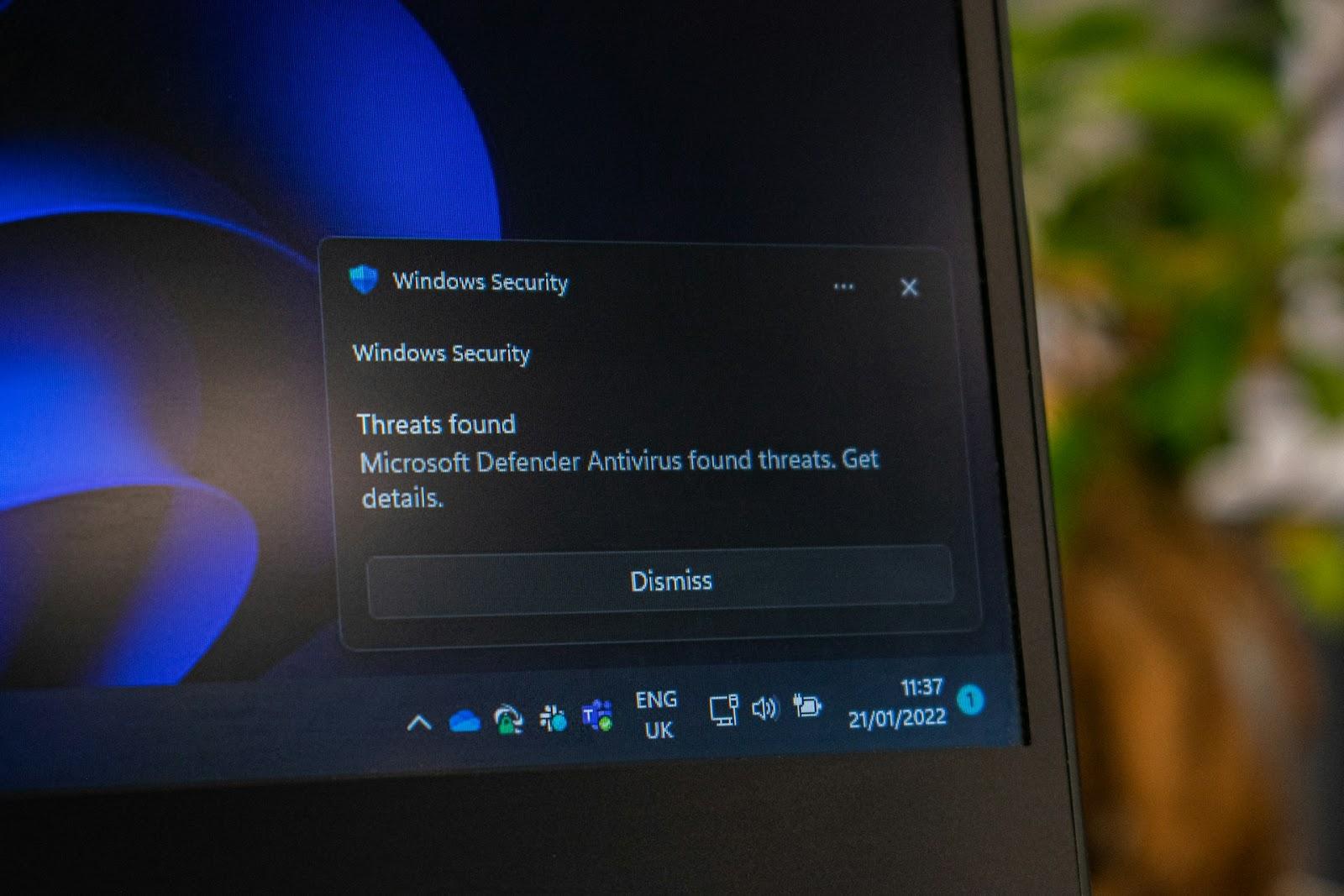
Anti-malware solutions offer real-time scanning, scheduled system checks, and automatic threat removal capabilities to identify and quarantine suspicious files before they execute.
Trusted solutions like Malwarebytes[2] or Bitdefender[3] offer both free and paid tiers with varying levels of protection. Free versions generally offer basic protection, while premium versions may include additional features such as:
- Firewall protection to monitor network traffic
- Email scanning to detect phishing attempts
- Web protection to block harmful websites
- Regular definition updates to identify new threats
It's generally advisable to schedule regular full system scans—weekly or biweekly—even if real-time protection is enabled. This practice can help detect dormant malware that might have slipped through initial defenses.
Practice Safe Browsing and Download Habits
Many people unknowingly expose their devices to risk by downloading files from unverified sources. This remains one of the most common ways malware spreads.
When downloading software, choosing official app stores and verified developer websites is typically safer than trusting third-party sources. Developers directly control distribution on their sites, reducing tampering risks, while it’s much easier for criminals to repackage popular software with hidden files or programs on third-party sites.
Besides shady downloads, you should always be wary of phishing emails that appear to come from legitimate entities but contain harmful links or attachments. It’s important to:
- Verify sender addresses carefully for subtle misspellings indicating spoofing
- Hover over links to preview the actual URL before clicking
- Be skeptical of urgent/scare tactics demanding immediate action (e.g., "Your account will be closed!")
- Avoid downloading suspicious files from unknown senders
Secure Your Network

An unsecured network acts like an open door for malware. One compromised device on the network can infect every connected smartphone, laptop, and smart home gadget on your network.
Hackers target vulnerable routers to redirect your internet traffic, inject malicious code into websites you visit, or even hijack connected devices like security cameras. However, you can significantly strengthen your router’s security by following a few basic steps:
- Start by updating your router’s firmware through its admin panel (usually accessible via 192.168.1.1)
- Change the default admin password to something complex
- Enable the WPA3 security protocol (or WPA2 if unavailable)
- Disable WPS and UPnP features, as these are known for being vulnerable to cyberattacks
- Disable remote management features to prevent external tampering
As an extra security step, you can also enable your computer’s built-in firewall, which monitors incoming and outgoing connections and can be configured to block unknown incoming connections. You can adjust firewall settings on your Windows computer through the Firewall & Network Protection option inside the Windows Security app[4]. Mac users can turn it on under System Settings > Network > Firewall[5].
Regularly Back Up Important Files
Backups are an important preemptive strategy, providing a crucial safety net should your system become compromised. You should ideally maintain multiple copies of important data on different media types (for example, external hard drives and cloud storage).
It’s also recommended that automated backup solutions be run on schedule. Most cloud services and operating systems offer options for scheduling backups. When choosing cloud storage services, look for ones with strong encryption and a reputable track record.
Why Basic Security Isn’t Enough (and How To Minimize Financial Damage)
Malware prevention best practices can significantly reduce the likelihood of unauthorized access to your accounts or information. However, these methods can’t protect your information after you’ve shared it with a third party, like you do when shopping online. In case the third party suffers a security breach, information such as your payment card number might be stolen by hackers.
To add a layer of protection in case of data breaches and other security compromises that could result in payment fraud, consider using virtual cards for all day-to-day transactions. These cards hide your real card numbers by generating unique, disposable numbers and CVVs. If a merchant suffers a data breach or a malware infection, your actual payment card information cannot be compromised.
Dedicated virtual card providers like Privacy further enhance this protection with additional features such as custom spending limits and advanced card controls, without requiring you to open a new account at any specific bank.
Stop Financial Fraud Before It Happens With Privacy Cards

Privacy is a BBB-accredited virtual card provider that enables you to seamlessly generate randomized 16-digit virtual card numbers after linking a debit card or bank account. Beyond hiding your real card numbers, Privacy gives you real-time control over your transactions. You can:
- Set spending limits to avoid overcharges or unauthorized transactions
- Pause or close cards instantly if you notice any potentially suspicious activity
- Get live alerts whenever your virtual cards are used or declined
Privacy lets you create four types of virtual cards:
Robust Security and Fraud Protection
As a PCI-DSS-compliant company committed to upholding the highest payment security standards, Privacy follows the same rigorous standards as major banks. By integrating the following security and fraud protection measures, Privacy ensures your sensitive data is protected from evolving cyber threats:
- Data encryption—Your sensitive information is encrypted using AES-256, both at rest and in transit. This is the same standard used by governments and financial institutions, and it ensures your data remains unreadable even if intercepted.
- Two-factor authentication (2FA)—Privacy lets you add a second authentication method, significantly reducing the risk of unauthorized access even if your login credentials are compromised by malware or phishing.
- Secure firewalled servers—Privacy’s systems are hosted on isolated, single-tenant servers with strong firewalls and regular security updates.
- Easy dispute mechanisms—If you notice unauthorized transactions, you can file a dispute quickly, and Privacy’s team will investigate and file a chargeback if it finds grounds for it.
Bonus Convenience at Your Disposal
Beyond comprehensive financial protection, Privacy offers various tools to simplify everyday transactions:
- Privacy Browser Extension—Available for Chrome, Firefox, Edge, Safari, and Safari for iOS, this extension allows you to create and autofill virtual cards with a single click, eliminating the hassle of manual entry.
- Privacy App—Manage cards, adjust limits, or pause transactions on the go with the Privacy App for Android or iOS, ensuring real-time oversight from anywhere.
- 1Password Integration—Create and store Privacy Cards directly within 1Password’s vault, streamlining secure payments without switching apps.
- Card Sharing—Safely share your virtual cards with trusted friends and family while keeping all spending controls.
- Card Notes—Attach reminders or labels to transactions, making it easier to track subscriptions and other purchases.
Start Using Privacy for Free
Privacy makes it easy to generate your first virtual card. All you need to do is:
- Visit the signup page and create your account
- Enter the required Know-Your-Customer (KYC) information
- Connect a funding source (bank account or debit card) with your Privacy account
- Request and generate your first virtual card
Privacy offers four monthly plans that you can check out below:
Resources
[1] Sitelock. https://s3.us-east-1.amazonaws.com/sectigo-sites-web/global/uploads/2022-SiteLock-Website-Security-Report-FINAL.pdf, sourced May 7, 2025
[2] Malwarebytes. https://www.malwarebytes.com/, sourced May 7, 2025
[3] Bitdefender. https://www.bitdefender.com/en-us/, sourced May 7, 2025
[4] Microsoft. https://support.microsoft.com/en-us/windows/firewall-and-network-protection-in-the-windows-security-app-ec0844f7-aebd-0583-67fe-601ecf5d774f, sourced May 7, 2025
[5] Apple. https://support.apple.com/en-in/guide/mac-help/mh11783/mac, sourced May 7, 2025
